In the realm of cybersecurity, digital data stands as a prime target for malicious actors driven by financial gain or other motives. In this article, we embark on a comprehensive exploration of data security, delving into strategies to safeguard your device against cyber threats.
Detecting and removing malicious spyware: Signs that your device has been hacked and ways to remove malware
One prevalent tactic employed by spyware is keystroke monitoring, commonly known as "keylogging." Hackers utilize a variety of malware, including ransomware and spyware, to execute their objectives. Keystroke monitoring involves covertly recording keyboard inputs, posing a significant threat to digital privacy. But how can we detect the presence of such malware on our devices? And what measures can we take to eliminate them? These questions will be addressed in the subsequent discussion.
What types of malware do hackers use?
Hackers use different types of malware, the most common of which are:
- Ransomware: Encrypts your data and demands a ransom to decrypt it.
- Spyware: Monitors your activity on the device and records what you type on the keyboard.
How do you detect that your device is infected with spyware?
- Slow keyboard response.
- Programs or files appear that you do not remember installing.
- Changes in device behavior, such as sudden restart.
- Receive suspicious emails or text messages.
- Data consumption has increased significantly.
- Note unusual activity on your social media accounts.
Risks of device hacking:
- Theft of personal and financial data, such as credit card numbers or bank accounts.
- Use the device to spread malware.
- Your device is controlled remotely by cyber attackers.
- Blackmail you using your personal information.
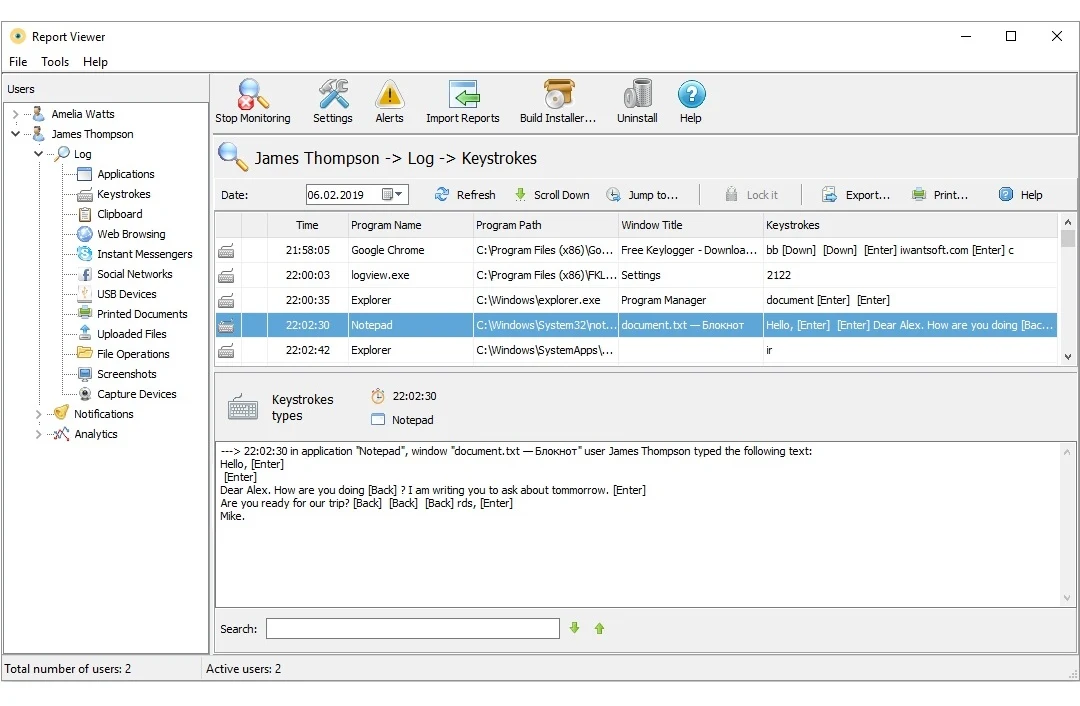
What are keylogger spyware?
Keylogger programs fall under the category of spyware, as their purpose is to acquire sensitive information like login credentials, passwords, and financial data. They achieve this by tracking input activities carried out on the keyboard and mouse linked to the computer.
How do keyloggers work?
Spying on computer input operations can be accomplished through two common methods. The first involves dedicated hardware devices that directly connect to the computer via USB or keyboard cable. The second method relies on specialized programs and applications installed and concealed within the computer to monitor keyboard activity.
- Hardware Approach: A dedicated device is inserted into a USB port or keyboard cable to log each keystroke.
- Software Approach: A program is installed on the computer to capture all user inputs.
Keyloggers are popular due to their ease of installation and difficulty in detection. Cyber attackers often employ phishing or social engineering tactics to deploy these programs on victims' devices. For instance, they may send links via email or text messages posing as reputable public figures or organizations.
 |
| Keyboard Detectors for Windows |
Is using keylogger spyware illegal?
When an attacker manages to infiltrate a victim's device and install keylogger software, the program begins recording every keystroke the user inputs on the keyboard, as well as mouse clicks. This data is then sent to the attacker, who can subsequently access passwords and personal information entered by the user.
Keylogger software is used in many illegal activities such as stealing personal data and passwords. However, some institutions and companies may legally use this type of software for specific purposes. For example, keylogger software can be used to monitor the activities of employees on company computers, ensuring that the devices are not used for personal purposes during working hours.
Furthermore, keylogger software can be used to enhance information security in companies, allowing administrators to track and record user activities on company computers. This can help reduce the risks of breaches and the leakage of confidential information.
Signs of a hidden keylogger: How can I tell if my computer is infected with a keylogger?
Keyloggers usually work invisibly and uncovertly, which means they don't appear on the screen or show any obvious signs of their presence. However, it may affect the performance of the computer, and some signs that indicate its presence can appear such as:
- Slow performance of your browser or device in general
- Delayed mouse or keyboard response.
- The mouse pointer disappears every now and then during use.
If you notice any of these signs, your device may be infected with keyboard detector. Of course, there may be other reasons for changing computer performance, such as various technical failures, but malware, including keyboard detectors, remains among the most likely possibilities. Therefore, it is important to carefully examine the device and look for any potential detection software that may be hidden inside it.
How to detect keylogger programs on computer
Detecting spyware that utilizes dedicated keyboard detection devices can be straightforward and logical. Simply observing any unfamiliar devices connected to keyboard cables or plugged into USB ports on your computer can reveal potential spyware installations. However, identifying keyloggers is not as straightforward and may require more proactive measures. To confirm whether your device is infected with a keylogger, follow these steps:
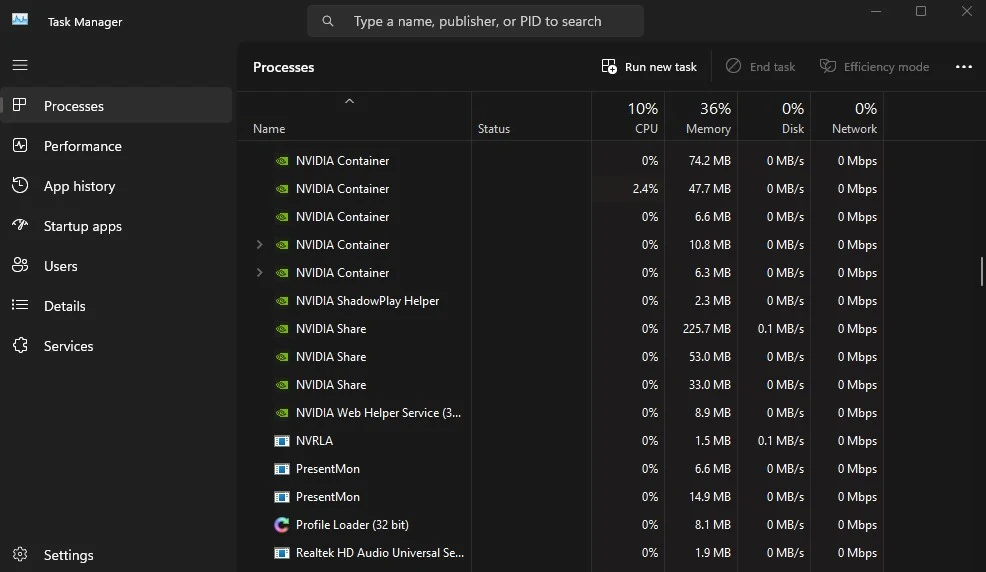
1. Check Task Manager
 |
| How to Detect Keylogger Software and Remove It — A Simple |
Malware software behaviors that are beyond users' control, rendering any abnormal activity on their device a significant sign of potential compromise. Windows users can utilize the Task Manager to pinpoint background applications and processes, a pivotal step in identifying keylogger software within the system.
By utilizing the Task Manager, users can effectively uncover any suspicious applications or anomalous activities running covertly in the background, thereby facilitating the detection of programs attempting to spy on their computer activities.
- You can easily open the "Task Manager" tool in Windows, either by accessing the menu that appears after right-clicking on the taskbar or by pressing the Ctrl + Shift + Esc keys.
- Upon opening it, thorough examination of both the "Apps" and "Processes" lists is necessary to identify all running processes and applications. If you encounter a suspicious process or application, you can simply terminate it by selecting it and clicking "End task."
However, you should be careful not to accidentally terminate important operations such as updating system files or other applications. These updates usually happen automatically. You can check the names of processes and apps via a simple web search to see if they are secure. You can also use a program to edit text and start typing, while monitoring which operations may be active as you type.
2. Find unknown applications on your device and scan installed programs
It's important to review your applications for any signs of suspicion. If you come across an unfamiliar app, it could potentially be a sophisticated Keylogger program. Many smartphones provide the option to inspect installed apps by accessing their "Settings" and navigating to the "Apps" section. Similarly, on your computer, you can utilize the "Add or Remove Programs" feature in the Control Panel to identify installed applications.
It is also recommended to check the list of applications and programs installed on the computer. You can do this by:
- Press the "Start" button
- And go to the "Control panel".
- Then click on "Programs".
- Then click on "Programs and Features".
When you find an app or program that you don't remember installing, it might be a key-detector program. Malware and spyware are often disguised as a phishing application with another name that has nothing to do with its true purpose in order not to arouse suspicion.
You can type the name of the application or program you suspect in the web search engine to verify that it is not one of the programs related to the operating system. Through it, you can know the nature and purpose of this app. If you're still suspicious about it, you can uninstall the app to make sure your device is safe.
Scan the computer using a powerful antivirus program
After reviewing the task manager and the list of installed apps and programs on your computer, the next step is to conduct a thorough scan using an up-to-date, robust antivirus software.
Advanced antivirus solutions such as BitDefender Total Security or Norton 360 are adept at detecting most keyloggers, even if they are concealed in obscure locations on your computer.
Certain antivirus programs may feature specialized tools tailored to identify keyboard monitoring software, enabling a comprehensive scan of your entire system. Upon detecting malware files, the antivirus software offers options to remove and eliminate them from your device.
Removing Keylogger Spyware on Your Computer: Effective Steps to Protect
Removing keylogger programs manually involves uninstalling suspicious applications from the Control Panel's Programs list. However, keylogger software might persist as hidden files elsewhere on the device. Thus, the most effective solution is to perform a thorough device scan using updated antivirus software.
Malicious software may also embed itself within the cluttered temporary files folder, complicating detection. It's advisable to regularly clear this folder:
- Open the "Settings" application on your computer.
- Go to the "Storage" section.
- Select "Temporary files."
- Choose the files you want to delete from the list and click the "Remove Files" button.
If manual removal of keylogger programs becomes challenging or antivirus software fails to eliminate them, resetting the device to factory settings may help. This action can eradicate keylogger programs and other spyware, restoring the system to its default state. However, keep in mind that resetting will delete all stored data, so backing up important files is crucial.
Preventing infection by keyloggers and spyware relies on proactive measures, such as installing robust antivirus software and keeping it updated. Basic protection programs for the operating system should also be updated regularly. Additionally, system and application software should be updated promptly to address security vulnerabilities. Users should exercise caution when browsing the internet, downloading files, and avoiding clicking on untrusted links in emails. Furthermore, removing or updating unused applications and old software is recommended, and caution should be exercised when connecting peripheral devices of unknown origin to the computer.