QR codes have become ubiquitous, serving as a primary tool for data sharing without physical contact. They provide instant access to information, such as websites, without the need for manual input. Users can use QR codes to log into Wi-Fi networks or access websites without passwords.
With the widespread use of QR codes in various aspects of life, cybercriminals have exploited them for fraudulent activities. In this article, we'll explore how internet criminals use QR codes in phishing email messages and how you can protect yourself.
What are the malicious uses of QR codes in emails?
Kaspersky has documented numerous email campaigns containing QR codes that redirect users to fraudulent phishing pages. For instance, a campaign towards the end of 2021 mimicked emails from delivery services like FedEx and DHL, tricking users into paying fees by scanning the QR code received in the email.
The encrypted link redirected users to a fake page for entering their banking card details. However, this campaign was not widespread and diminished by mid-2022.
Then, in the spring of 2023, Kaspersky recorded a new campaign exploiting the names of major tech companies, such as Microsoft or its cloud service Office 365. The email messages urged users to take action, like scanning the QR code to maintain account accessibility, with a notice claiming their account password was about to expire, risking losing access to their inbox. Therefore, they needed to change the password by scanning the QR code in the email and following the instructions.
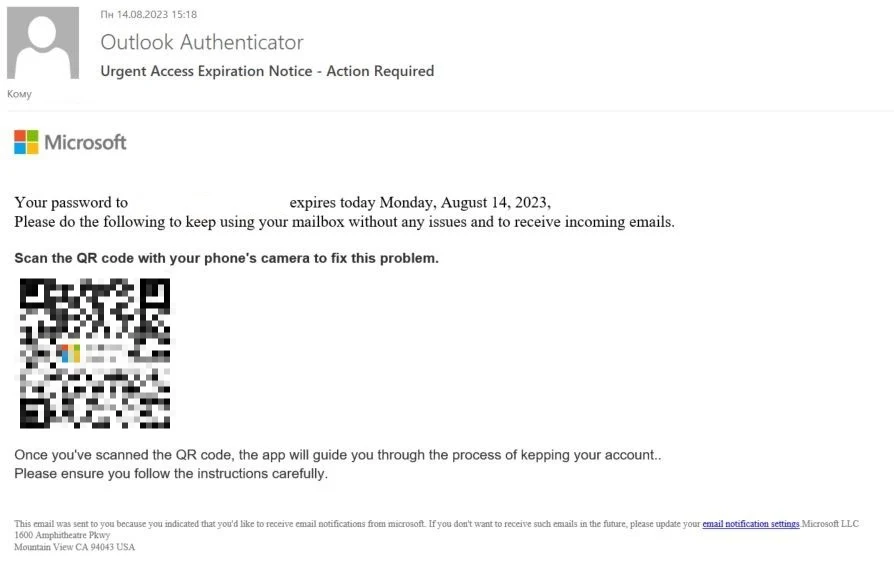 |
| A message urging the user to reset the password by scanning the QR code. |
Another email message may warn the recipient that "their authentication session has expired today," and to avoid this, the user must quickly scan the QR code at least using the smartphone to recheck the password security, otherwise they will lose access to their account permanently.
Another example: the message may kindly tell the reader: "This email message is from a trusted source" so that the user abandons his caution, and the thrust of the message indicates that it is assumed that (3 important emails) could not be delivered to the user due to a problem with (email validation). Of course, scanning the QR code at the bottom will solve the problem.
It's clear that the authors of these email messages aim to prompt inexperienced users to take quick actions out of fear of losing their accounts. They may also hope that mentioning authentication apps, which already use QR codes, could create some mysterious associations in the recipient's mind.
What happens if you scan the QR code in the email?
Scanning the QR code takes you to a somewhat convincing replica of a Microsoft login page, and naturally, all the data you enter on these phishing pages ends up in the hands of internet criminals.
The interesting detail is that some phishing QR code links lead to IPFS resources, a file-sharing protocol similar to torrents, allowing file distribution online without domain registration, hosting, or other complexities.
In other words, the phishing page resides directly on the scammer's computer and can be accessed via a link through a private IPFS gateway. Fraudsters use the IPFS protocol because it's easier to deploy, and removing a phishing page is much harder compared to blocking a harmful website. Consequently, these links persist longer.
Protecting against QR code phishing:
A good authentication system won't rely solely on scanning a QR code, so if you receive an email asking you to confirm something, log in again, reset your password, etc., and it contains only a QR code, it's likely a phishing attempt. Safely ignore and delete such emails.
When you need to scan an unfamiliar QR code, security experts from Kaspersky recommend using Kaspersky Premium with its embedded Safe QR Code Scanner. It verifies QR code contents and warns you if there's anything fraudulent within.
What is a QR code?
QR codes have become ubiquitous, appearing on posters, leaflets, ATM screens, price tags, merchandise, and even historical buildings. While people extensively use QR codes for sharing information, promoting online resources, making payments, and verification, their presence in emails is limited. Users tend to read emails on their phones without a scanning device readily available, leading to the prevalence of ordinary hyperlinks in most emails. However, attackers are increasingly utilizing QR codes in email-based attacks.
In contrast to easily verifiable and blockable phishing links, QR codes pose a challenge for security solutions. Analyzing QR codes requires expensive and resource-intensive computer vision technology to decipher the information they contain. Moreover, unlike regular links that can be assessed visually, the destination of a QR code remains unknown until scanned.
What exactly is a QR code? Also known as a Quick Response code, it is a 2D matrix barcode featuring squares and dots arranged on a white background. Image processing devices can scan QR codes by identifying the code's location through squares and then reading the encoded information in the dots. Beyond functionality, QR codes can include decorative elements like a company logo within the square field.
Notably, QR codes excel at encoding more data than traditional 1D barcodes, making them ideal for hyperlinks to diverse resources like store catalogs, checkout pages, or informational building pages.




